Ebay and wish.com are full with surprisingly cheap “too good to be true” sd cards. I have decided to take my chances and buy 2 most likely fake sd cards from wish.com
I deliberately choose one that appeared a little bit more expensive comparing to the rest of the cards, in the hope that the actual fake cards are not the worst of the worst quality. So I ended up hitting on this ad:
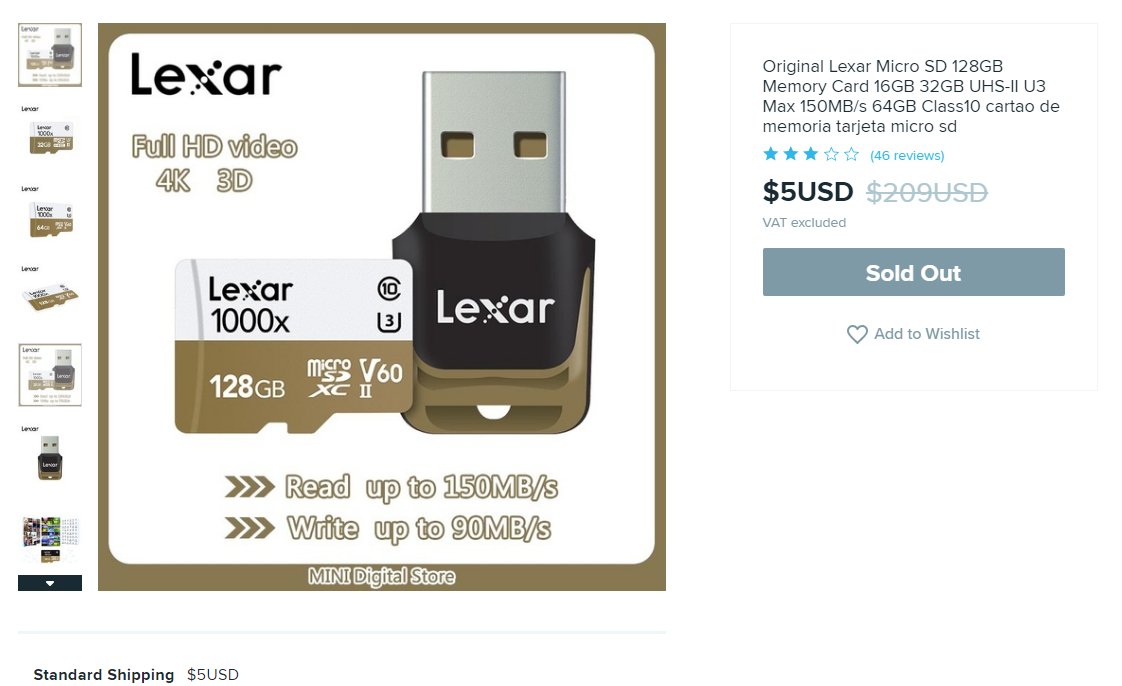
So this “Lexar” card was for $5 +$5 shipping adding up to $10 / piece. I bought 2 of these, and a wish.com special is no matter how many items you purchase you get charged for shipping regardless of how many would actually fit in a single jiffy for shared posting. So I ended up paying $20 for 2 most likely fake cards.
couple of weeks later the cards have arrived. And after unpacking the first thing i’ve noticed is it didn’t come with the usb card reader. it was just the card itself in a very convincing looking packaging.

After unpacking the actual SD card looks pretty damn convincing still. The etching on the card looks flawless as well.
Now the way they make these fake sd cards is they pick up a smaller sized ones, and they somehow edit the otherwise read only part which presents the actual total size. So they pick a small and usually slow sd card and they bump it up to 128G size. As these cards have “some amount” of actual working storage, if you end up using it in a phone or camera and you only start to fill with pictures slowly by the time you notice that it’s fake, the sellers are all gone from wish.
Now my plan was to get a 2-4G card i can use with a raspberry pi. Testing these cards are not actually simple because under windows whatever i copied to them got cached, and it looked “healthy” as long as i didn’t pull out and plug back in. I’ve ended up trying this out with a program called f3 I’ve run it on a linux vm, and in matter of seconds I got the results which I’ve expected.
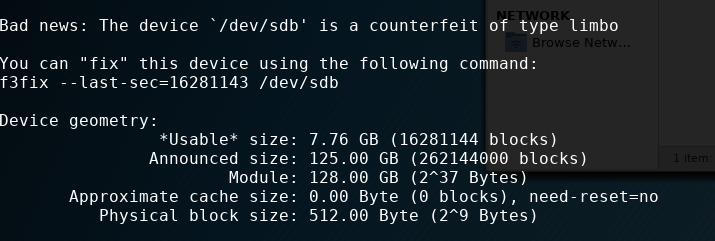
So as per the tests above the fake card has 8G usable space which is more than enough for what I needed it for. The only problem I had is I couldn’t use “noobs” to deploy raspbian because it wanted to resize my card to 128G, I had to deploy it manually to a 7G partition.
With the evidence above I’ve openned a ticket with wish.com and about 2-3 messages back and forth I’ve received a full refund including shipping as well.